CRYPTOGRAPHY OR STENOGRAPHY BY USING SOFTWARE AND CMD PROMPT:
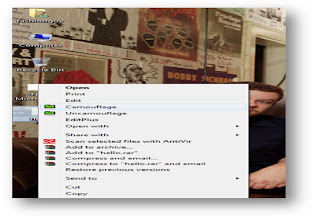
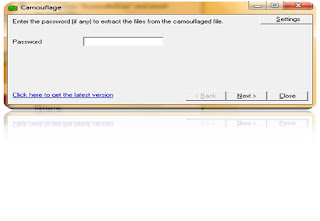
Using Cmd prompt: Step 1: open cmd prompt Step 2: type command copy /b picturename.jpg+filename.txt final.jpg Step 3: it will show same picture as like before only but file will be hided at back of the picture. Step 4: now we want to open that same file again. Then open that picture with notepad then it`l show our data at the end of the file. note: this command will not work on win7,vista. picture and file be in same directory using software tool: Step 1: download the software by clicking this below link. Step 2: now install in your computer. It's not a virus it'll not harmful to your computer also. Step 3: Create a notepad file like this and save as hello.txt Step 4: now right on the file and open with Camoflauge option Step 5: do the operations as like below process. Step 6:attach file with any picture or software. Step 7: enter your unique password to protect from others. Step 8: finally resultant file will be like as show in figure. Step 9: now again we want to retrieve that same file then right click on that file and open with uncamouflage . Step 9: enter password and extract ur file into ur machine.
Camoflauge

 1:17 AM
1:17 AM
 vijay & nag
, Posted in
vijay & nag
, Posted in